
Chain Double Protocol
Chain Double is a backwards-compatible protocol that combines IPFS and cross-chain message passing to trustlessly expose on L1 NFTs the result of actions taken on L2.
Introduction
In the current landscape of NFTs, the most common method to associate media, like images, with NFTs involves pointers to off-chain storage solutions such as IPFS or, in less ideal scenarios, centralized servers. This method introduces a significant risk due to the potential separation between the NFT's on-chain presence and the media it represents. This approach lacks certainty in maintaining the integrity of the link, as both IPFS and centralized servers are susceptible to data loss. IPFS nodes can delete data arbitrarily, and centralized servers are vulnerable to various well-known issues.
Drawing inspiration from the operational principles of rollups, where intensive computations are offloaded to more economical L2 networks and then 'timestamped' on L1, the Chain Double Protocol computes NFT metadata on an L2 network and, at the owner's discretion, records these changes on L1 using a mix of message passing and IPFS.
This approach allows owners to interact cost-effectively with their Chain Double tokens on L2, opting for L1 gas expenses only when it is economically justified, such as before a token sale or for display purposes.
Targeted towards engineers, this document explores the inner mechanics of Chain Double, elucidating its operational framework and the technical intricacies that make it a pioneering solution in the blockchain space.
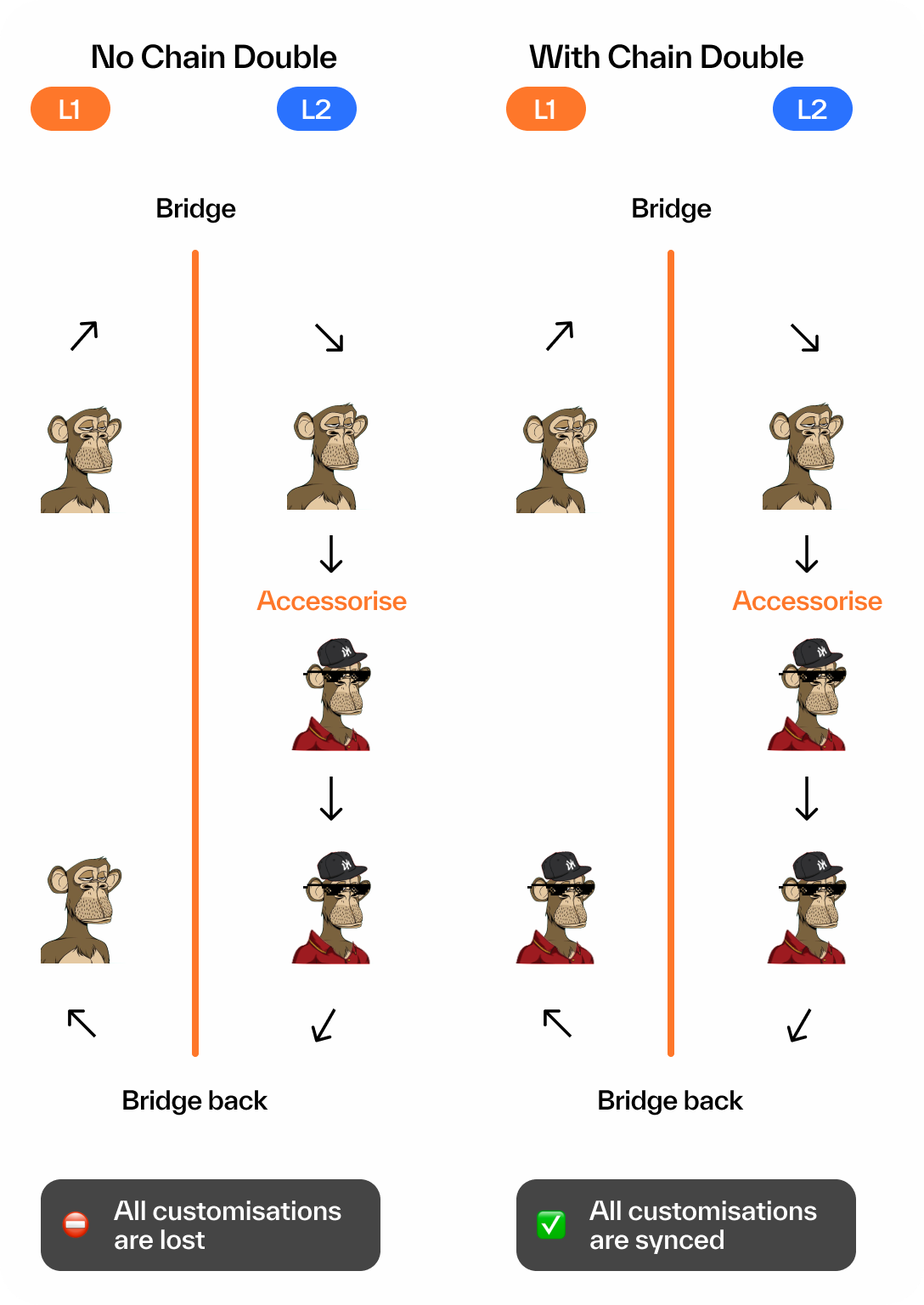
Why Chain Double?
The film industry, known for its art of illusion, often relies on the lesser-known stunt double to undertake significant risks while the celebrated actor receives the glory. Quentin Tarantino beautifully illustrates this dynamic in his last film.
The Chain Double concept mirrors this cinematic technique: the cost-effective L2 token does the substantial work, ensuring the valuable L1 token remains impressive and valuable.
Core Mechanics of Chain Double
Integral Components
Chain Double adopts a dual-layered structure for NFT management:
- NFTs on L2: Designed for active engagement, these NFTs have fully on-chain metadata that can be updated or altered through user interactions.
- NFTs on L1: Serving as a more static representation, they selectively reflect updates from L2, based on the owner's decisions.
- IPFS Uploader: This permissionless and trustless role, open to any L2 observer, involves uploading the latest metadata state to IPFS following an L2 NFT update.
Technical Specifications
Deterministic IPFS CID Generation
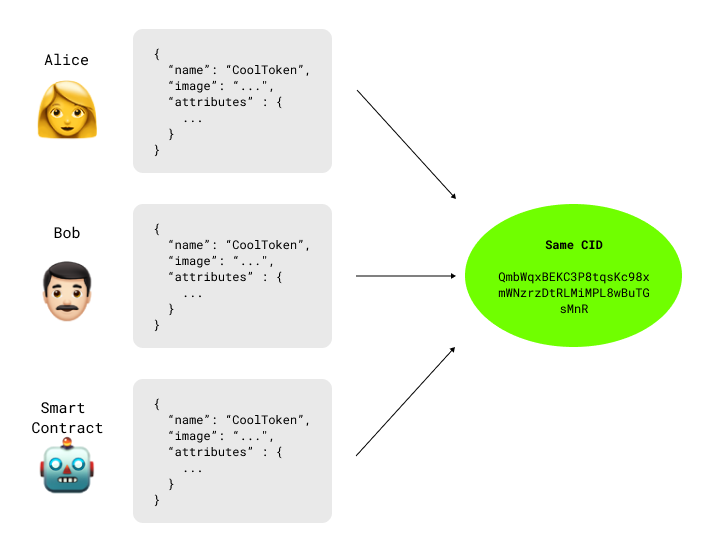
IPFS employs deterministic identifiers, known as CIDs, generated by IPFS's hashing algorithm. This ensures that identical files uploaded by different users always produce the same CID.
Chain Double leverages this feature for L2 NFTs, allowing the use of the IPFS hashing algorithm to compute the IPFS CID. This mechanism provides a snapshot of the current state that can be securely 'locked' into L1 at the owner's discretion.
Metadata Synchronization
With a CID representing the current metadata state, it's necessary to securely transmit this CID to L1 and link it to the L1 NFT. Any secure cross-chain messaging service can be used to transfer the CID, with the protocol remaining agnostic to the service choice.
Upon reaching L1, the messaging system updates the L1 NFT's URI by executing the setTokenURI method.
IPFS Upload
Updating the L1 NFT with the new CID is crucial, but the metadata must first be uploaded to IPFS. Until this is done, any L1 observer would encounter a non-functional IPFS link. However, since the metadata on L2 is fully accessible, anyone can extract and upload it to IPFS, resulting in the generation of the corresponding CID.
Advantages and Engineering Implications
Previously, NFTs requiring extensive interaction were confined to L2 deployment, missing out on the security and value of L1. Chain Double offers a solution, enabling developers to enjoy the benefits of L1 without sacrificing interactivity. For instance, gamers can play extensively on L2 and update their L1 tokens following significant achievements. Similarly, decentralized social media users can post regularly and update their L1 profiles only before crucial events.
Like rollups, Chain Double offloads much of the workload to more economical solutions without compromising final security, achieving a similar goal for NFT metadata.
Test the Concept
A simple repository and demo have been created to demonstrate the protocol's viability. The code and demo are available for exploration.
Collaboration Invitation
The development of the Chain Double Protocol is an ongoing process. Contributions towards evolving it into a comprehensive EIP standard are welcome. Engineers and blockchain enthusiasts are invited to join this innovative venture.